Vidar is a relatively new keylogging, data-stealing malware campaign. It is generally distributed through malicious advertisements, a common hacking technique, on less-than-reputable sites such as bit torrent or free video streaming sites. These malvertisements redirect their victims to various exploit kits such as Fallout and GrandSoft, which in turn will infect your machine with various malevolent payloads such as Vidar.
How it works
Vidar is sold or rented as a service to the blackhats. For the low price of $700 they are able to utilize Vidar’s distribution system to spread their own malware. They can even customize it to steal a variety of your sensitive data such as browser history, website logins, credit card numbers, and cryptocurrency wallets.
One of the more common payloads is the ransomware called GandCrab. Ransomware is exactly what it sounds like – it encrypts your files and demands payment in order to decrypt them. SUPERAntiSpyware detects many variants of the GandCrab ransomware. Our researchers are hard at work daily to detect more variants and help combat this threat.
Unfortunately once your system becomes infected with ransomware like GandCrab, there are few options for you. You can either pay the ransom and hope they unlock your files, or you may get lucky and find that a decryptor has been created. Currently there are decryptors for some versions of GandCrab (V1, V4, and V5). It is worth noting that these decryptors, while definitely helpful, do not always work perfectly for all encrypted files. The final option is less appealing – wipe your system and reinstall Windows. The upside is that you should be able to use your computer again without paying. The downside is that you will have lost all your documents.
Our suggestion to protect yourself from ransomware is relatively simple: Back up your files. Being able to restore your important documents from a cloud or local backup is the best way to thwart a ransomware attack. Keeping your system up to date with software patches is also something we recommend to help protect yourself.
Who is affected
Due to the way it is distributed, Vidar does not target individuals or businesses directly. It relies on people clicking on their malicious advertisements. In general, you should avoid clicking ads online, no matter how enticing. Something interesting about GandCrab is that it has been known to check if you have a Russian keyboard layout, and if so it terminates its execution immediately.
Indicators of compromise
Vidar itself is very stealthy, doing its data thievery quickly and silently in the background. It’s very likely that you won’t even know that Vidar has hit you until it drops its payload. Vidar drops some text files onto your system into ProgramData\(random string)\ and ProgramData\(random string)\files\. These files contain passwords and other information that Vidar has stolen. There may also be a zipped file containing copies of these text files.
The most common malware delivered by Vidar has been GandCrab ransomware. Within a minute or so, GandCrab will change your Windows background to something similar to this:
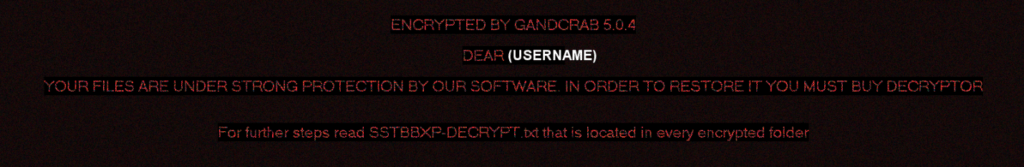
There will be an HTML or text file called (random)-DECRYPT dropped into every folder where files have been encrypted by GandCrab, containing instructions on how to pay the ransom to get your documents back. You will also notice that the encrypted files will have their extension changed to something random instead of the correct extension:
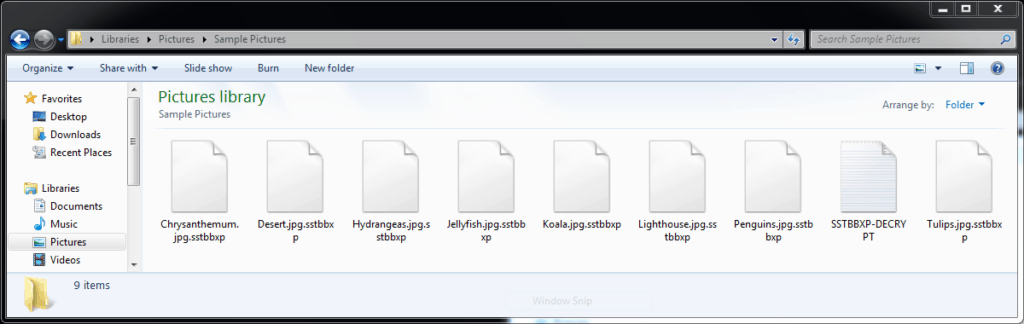
Here is a list of file types that may be targeted for encryption by GandCrab:
.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odt
What you can do
SUPERAntiSpyware detects many variants of Vidar, however new versions are being created all the time so make sure to always update to the latest database version. Also, upgrading to Real-Time protection will dramatically increase your level of protection from this threat.
Installing an Ad Blocker on your computer can help stop Vidar at its source, however one of the best practices is to refrain from clicking on any advertisements online.
If your files have been encrypted by GandCrab, you may still be able to decrypt them. Various companies and individuals create ransomware decryptors and release them on the internet. These decryptors are specifically designed to unlock files that were encrypted with a particular version of ransomware, so make sure to note the version of GandCrab when looking for a decryptor – the version we were infected with was 5.0.4. No More Ransom is a repository of most of the decryptors available and is always being updated.
If you are not able to find a decryptor that works, SUPERAntiSpyware suggests that you do not pay the ransom. There is no guarantee that the blackhats will unlock your files once they receive your payment. In 2018 it was reported that paying the ransom actually gets your files decrypted less than 50% of the time. If your data is extremely crucial, we suggest you contact a company who specializes in data recovery services.
HOW TO REMOVE Vidar/GandCrab
- Using an uninfected system, search the internet for a decryptor for your particular version of GandCrab and copy it to a USB drive – I would suggest starting with No More Ransom
- Restart the infected computer in Safe Mode with Networking
- Insert the USB drive with the decryptor, copy it to the desktop, then eject and remove the drive
- Run the decryptor
- Assuming the decryptor is successful, update your SUPERAntiSpyware to the latest database version and run a complete scan to remove any traces of Vidar from your system
- If the decryptor does not work, you can take your computer to a data recovery expert

Thanks for the detailed instruction how to remove Vidar, which really insidiously attacks through ads .
There are very useful articles on anti spamming on your website.